26/01/23
The Proof-of-Stake Economy After The Merge
Category
Written by
Read time
25 min
In this piece @lingchenjaneliu explores the staking market landscape, including key actors and top players, as well as latest developments in Proof-of-Stake. Special thanks to @0xPhillan for reviewing and editing the piece!
For more of her content, subscribe to her newsletter Crypto Observe on Substack or subscribe to the Web3edge newsletter!
Contents
- Background
- Proof-of-Stake Economy Actors
- Key Players
- The industry is moving towards a permissionless model
- References
Background
The Merge of the Ethereum network took place on September 15, 2022, leading to changes in the fundamentals of the ETH asset. Now, holding ETH long-term has become even more attractive for investors due to the following reasons:
- Decreased ETH issuance: The most visible on-chain impact of the Merge has been the decreased issuance rate of ETH. With Ethereum’s update to Proof-of-Stake, the network drastically reduced the amount of new ETH issued with every block. In the long term, due to a burning mechanism introduced with the network upgrade EIP-1559, there’s a possibility that this may make Ethereum deflationary – meaning its token supply could decrease over time.
- Increased incentives to stake: After The Merge and with EIP-1559, Ethereum generates revenue from transaction fees (tips in gas fee) that were not available on the beacon chain. This revenue is incremental to the stakers and providers investors with a strong incentive to stake their ETH. Staked ETH is out of circulation and creates a strong support for the price of the ETH asset.
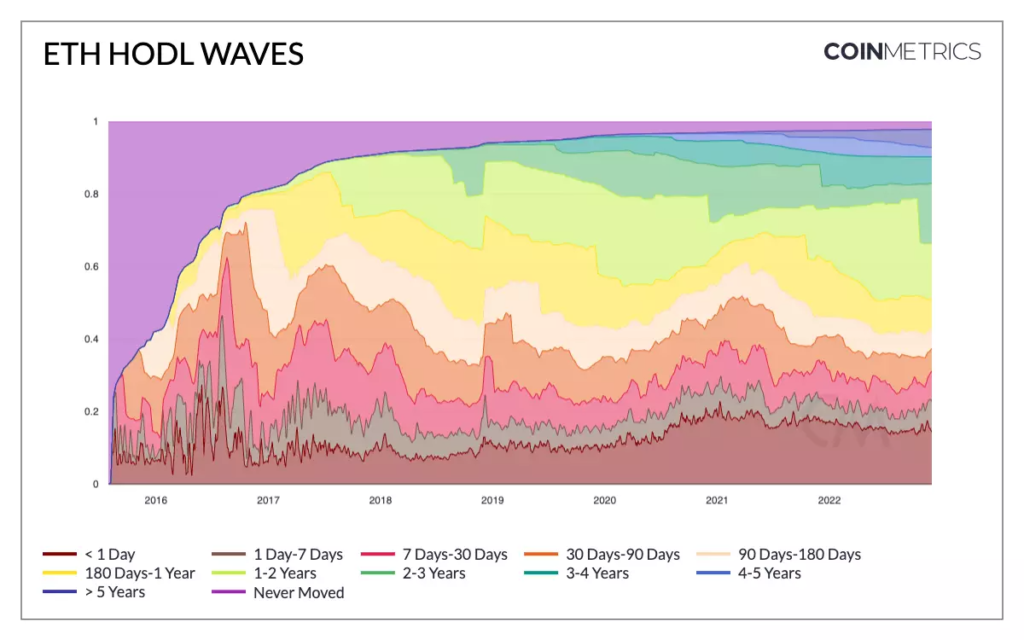
From figure 1, you can see that there are more long-term ETH holders after The Merge as holders have an expectation that in the long-term, the asset price will increase due to the reduced issuance and increased staking demand. After The Merge, the staking demands of investors have steadily increased to the benefit of the entire Ethereum staking economy. It is, therefore, worth scrutinizing the services and infrastructure that support the staking economy.
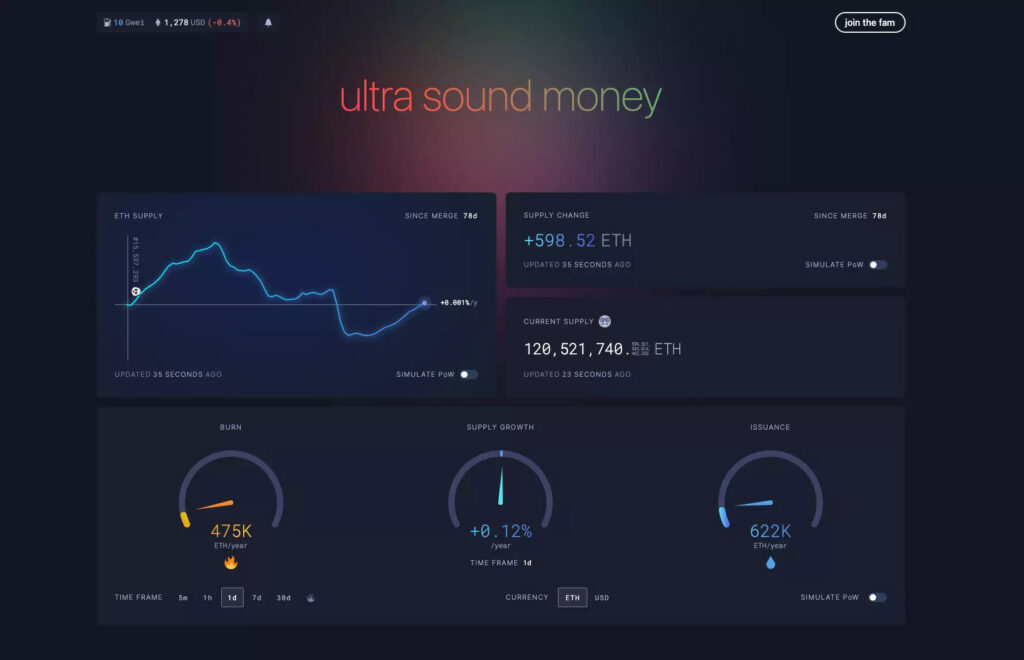
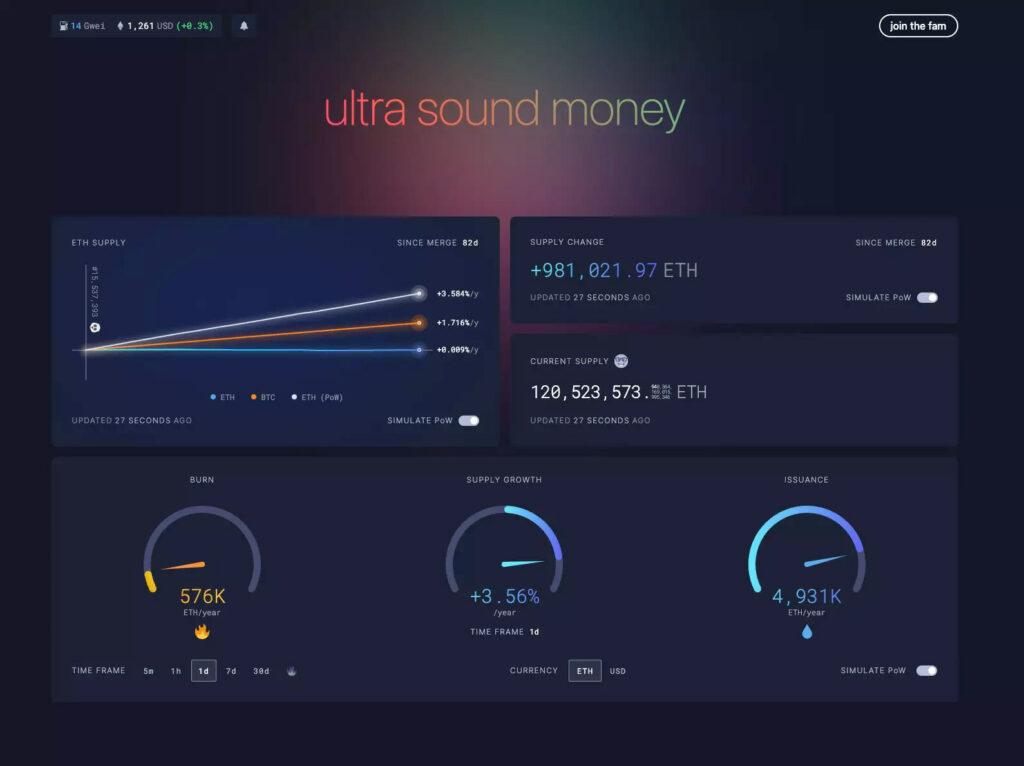
Comparing ETH issuance and supply numbers between figure 2 and figure 3, you can see how these numbers look if The Merge hadn’t happened. By doing that you can visualize the impact of the Merge on ETH issuance and supply growth: after the Merge, ETH supply growth is nearly flat, but if the Merge hadn’t happened, the simulated supply increase would have been +3.5%.
What Is the Merge?
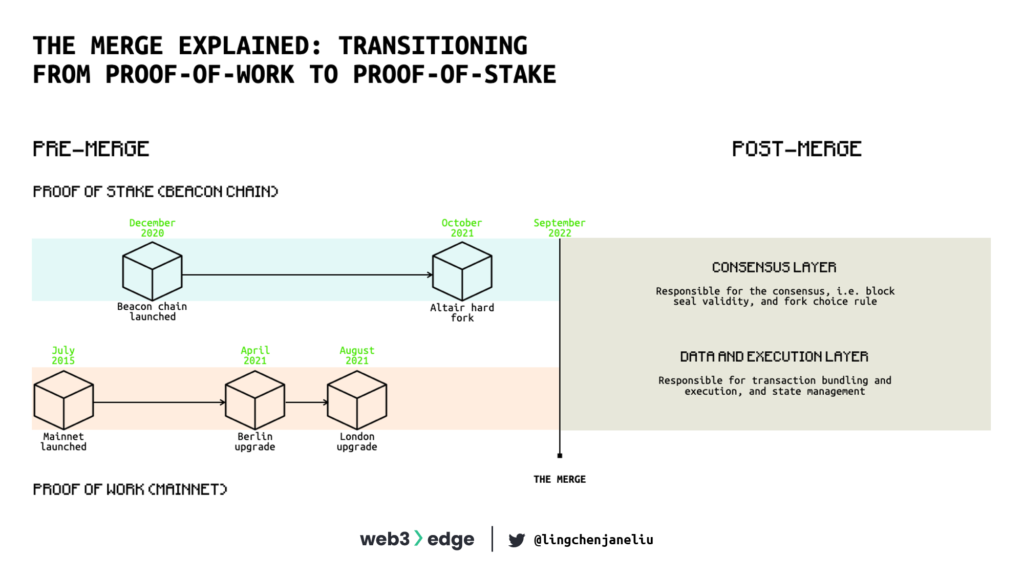
The Merge marks the most significant event in the history of the Ethereum network. When Ethereum was launched in 2015, the goal was for the network to be secured by a novel Proof-of-Stake consensus protocol, replacing the then-standard Proof-of-Work style security used by Bitcoin and its derivatives. But because Proof-of-Stake was a new concept, Ethereum opted to launch with Proof-of-Work and transition to Proof-of-Stake later, once they were confident they had ironed out the kinks.
To ensure the Proof-of-Stake chain would operates smoothly before launching it to the public, they launched it as a separate Beacon chain. “The Merge” is when the Beacon chain merged with the Proof-of-Work chain, completing the shift to Proof-of-Stake. This was achieved with no downtime of the Ethereum Mainnet. There are two parts to Ethereum post-Merge: a data and execution layer, and a consensus layer.
- Data and Execution Layer: Data and execution layer listens to new transactions that are broadcasted in the network, executes them in the Ethereum Virtual Machine (EVM), and holds a database and the latest state of all current Ethereum data archives.
- Consensus Layer: Consensus layer implements the Proof-of-Stake consensus algorithm, which enables the network to achieve agreement based on validated data from the execution client.
Why Switch to Proof-of-Stake?
The Ethereum Proof-of-Work chain was working fine, so why bother with the Merge and the shift to Proof-of-Stake? Proof-of-work is trusted and reliable, but it has its downsides. One is energy consumption. It secures the network by having the validators, also called “miners”, race to solve cryptographic equations to verify the next batch of transactions. If you win the race, you get paid for your efforts in the native network token.
If you don’t have state-of-the-art hardware, the chances of winning the computational race are extremely low, and mining activities as a whole are a wasteful use of electricity compared to validating in a Proof-of-Stake network, where validation operations are not based on who owns the most computing power.
That is a big part of what The Merge is doing. When Ethereum switched from Proof-of-Work to Proof-of-Stake, energy usage was estimated to drop by up to 99.98%. There won’t be any need for massive mining operations, anyone with a decently powerful laptop could run a staking validator if they wanted to, and they are not racing to solve computationally intensive problems so no unusually high amount of energy is required to contribute to the network. A computer running a validating node would not use much more energy than it would from normal use.
Proof-of-Stake Economy Actors
The Proof-of-Stake economy consists of a rich staking ecosystem as players participate in their part to secure the network. I broke down the Proof-of-Stake ecosystem, mainly focusing on node management services and staking-as-a-service providers, to introduce all the moving parts in the blockchain staking economy. Starting from explaining what node management services are and the delicate differences between centralized and decentralized ones, to explaining the differences between staking options and existing staking economy market landscape, I would like to help stakers better understand how the tools work that they use. Let’s start!
Node Management Services
What is a node?
A node is a device that runs an Ethereum client. A server stores, sends, and receives data. Multiple servers come together to make a network.
Ethereum is a distributed network of computers running software that can verify blocks and transaction data. To participate in the Ethereum network, you need to install software on your computer called a client to turn it into an Ethereum node.
What is a client?
In Ethereum, a client is a software that verifies data against the protocol rules and keeps the network secure. Clients come in different implementations, i.e., different software versions, that all follow the same protocol rules of the Ethereum network.
There are 3 different types of nodes that consume data differently in the Ethereum network: full nodes, light nodes, and archive nodes. I will examine these different types of Ethereum nodes used on the Ethereum blockchain and their differences.
- Full Nodes: A full node keeps a complete copy of the blockchain data, and contributes to the network by receiving transactions and blocks from other full nodes, validating them, and forwarding them to other full nodes. It requires decently powerful hardware and bandwidth to run a full node.
- Light Nodes: A light node is much smaller than a full node and does not participate in block validation in the same way. A light node stores block header data, such as the preceding block’s hash and a timestamp, rather than the complete block data like a full node does. Light nodes send on-demand requests to full nodes, validating only the parts of the state that their user’s require. Light nodes use the minimum amount of data possible to interact with the Ethereum blockchain, and outsource all the other information from full nodes. With each new light node, there is greater censorship resistance, corruption resistance, and prevention of centralization of the Ethereum network.
- Archive Nodes: Archive nodes store everything in the full node and build an archive of all historical states, the data capacity needed to run these nodes are very high so it is less desirable for typical users to run an archive node. However, it is valuable to service providers such as block explorers, wallets, and on-chain analytics companies. The difference between archive nodes and full nodes lies in the data storage span. Archive nodes contain all historical data since the very first block (known as the genesis block), whereas full nodes only store a snapshot of current state data, which is necessary for validating new transactions.
What is a validator?
Validators can be full nodes or archive nodes that participates in consensus, by receiving broadcasted transactions from full nodes and execute the transactions, validate their eligibility and achieve state consensus (on the consensus layer). To participate as a validator, a user must deposit 32 ETH to run three separate pieces of software: an execution client, a consensus client, and a validator. Validators play a key role in maintaining and securing blockchains. Validators, similar to miners in proof-of-work blockchains, are blockchain nodes in charge of processing, confirming and writing transactions into a new block. Every Proof-of-Stake based blockchain has validators who compete to perform those tasks in order to earn a share of the protocol’s revenue from transaction fees and from protocol’s security budget.
So after understanding aforementioned fundamentals of node, clients and validators, it is important to understand the concept of “node-as-a-service” infrastructure. When it comes to accessing the Ethereum network for building and operating decentralized apps, Web3 developers need to interact with node infrastructure to do so. There are three ways that developers could go about this:
- Running your own node.
- Leveraging centralized node infrastructure providers like Infura, and Alchemy.
- Leveraging decentralized node infrastructure infrastructure providers like Pocket Network or Ankr.
Running your own node
Running your own node requires you to run physical hardware at home that is connected to the internet 24 hours a day, 7 days a week with stable power supply and internet connection.
- Advantages: Receive full staking rewards, while improving the decentralization and security of the network and holding your own funds in the most secure way.
- Trade Offs: Labor, time and capital intensive. First, you need to deposit 32 ETH to activate validator software and become a validator node. Being a validator node means that you are responsible for adding new blocks, processing transactions and storing data. By providing security to the network, you will receive new ETH as reward. Second, you are in charge of the operation, which means you need to maintain, and troubleshoot the machine and networking. Technical understanding can be a barrier to entry for those without necessary technical knowledge.
Leveraging centralized node infrastructure providers
Microsoft Azure, Google Cloud, and Amazon Web Services (AWS) provide node infrastructure to run cloud-based operations housed in huge data centers. And we see those cloud providers also prevail in the Web3 world. According to crypto analytics platform Messari, “Three major cloud providers, AWS, Hetzer, and OVH, are responsible for 69% of the 65% of Ethereum nodes hosted in data centers.” Alchemy and Infura, accounting for 5-10% of Ethereum nodes, rely heavily on those three major cloud providers to host Ethereum nodes. A Web3 company that claims to be fully decentralized is not really operating in decentralized manner if it uses a centralized node provider like Infura even though Infura does make building on Ethereum a lot easier.
- Advantages:
- More Cost-efficient: Centralized networks are typically the most cost-effective options for small systems and require fewer resources to set up and maintain.
- Rapid Deployment: It is easy to add or remove client nodes from the network by just creating or removing connections between the client node and main server.
- Trade Offs:
- Power Concentration: If a centralized provider gains a majority of infrastructure control over a blockchain due to the number of nodes it operates, that could compromise the security and continuity of decentralized systems.
- Censorship: From recent (August 2022) Tornado Cash Sanctions, we can see centralized providers make it clear that they must comply with government regulations, which means dApps dependent on them are also subject to censorship.
- A Single Point of Failure: Centralized node infrastructure providers like Infura and Alchemy use AWS data centers exclusively to house their nodes. This creates a single point of failure: if AWS goes offline, the decentralized applications dependent on it will also go offline.
- Cases:
- Major Players: Infura, Alchemy
Leveraging decentralized node infrastructure providers
A decentralized network distributes workloads across multiple devices instead of relying on a one central server. Each of these separate devices interacts independently with other nodes. As a result, even if one of the master nodes crashes or is compromised, the other servers can continue providing data access to users, and the overall network will continue to operate with limited or zero disruption. In order to communicate with a network, a Web3 developer, software (dApps, Wallets, etc.) or user needs to communicate with a node and tell it to broadcast commands to the network. This is achieved through RPC (remote procedure call) commands. This is basically sending the server a command telling it do something specific, and the server will do it (e.g., broadcast specific transaction to network). The censorship aspect of centralized infrastructure means that the providers can screen the RPC commands they receive before letting their nodes broadcast them, and that way can effectively censor transactions.
Enjoying this piece? Subscribe to the Web3edge newsletter and never miss new content!
With Pocket Network and Ankr, that access to the RPC itself is decentralized, thus preventing individual nodes from declining RPC commands. Ideally, we would not need such infrastructure, as individuals should be spinning up their own nodes that they can use in a fully uncensored manner, but the heavy reliance on centralized infrastructure and the inaccessibility of running your own node has unfortunately made this necessary.
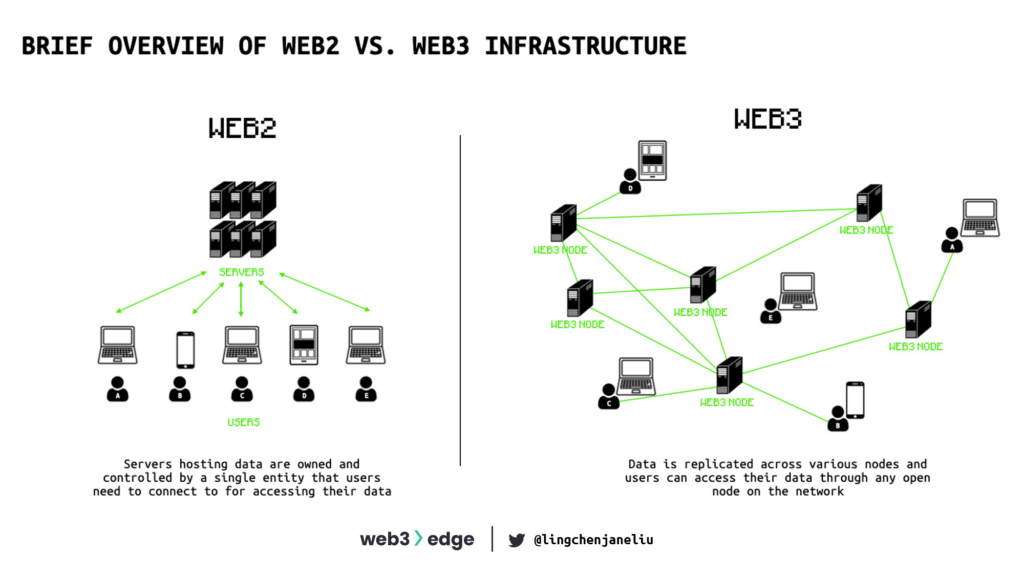
Difference in node infrastructure between Web2 and Web3?
In Web3, instead of accessing a closed network that is owned and operated by a centralized Infrastructure-as-a-Service (IaaS) provider, users access a public network that is operated by thousands of independent nodes that abide by strict rules defined in the code of the client software that run on all the nodes across the network.
- Advantages:
- Higher Flexibility: Decentralized networks can continue to operate even if a master node is compromised. Aside from that, it is easier for decentralized networks to scale as operators can simply add more nodes to the network to increase its decentralization and ensure sufficient command throughput capabilities.
- Privacy: Information saved on the network is disseminated across multiple points and this makes data flows more difficult to track across a network. On top of that, it will be more difficult for malicious actors to target specific information.
- Optimized performance: As opposed to routing connections over vast expanses to a single centralized server, network operators can create master nodes in regions where user activity is high.
- Trade Offs:
- High maintenance cost: A decentralized network relies on multiple devices to support the system so the maintenance will reply on the efforts of individuals to ensure sufficient up-time for the devices.
- Lower transaction throughput: Achieving optimal decentralization tends to decrease network throughput. As more miners secure a network through consensus, transaction speeds may drop.
- Major Players: Pocket Network, Ankr
Although there are still some technical challenges to overcome to attain higher transaction throughputs, we need to keep in mind that the power of the internet lies with the organization which holds the data. If the information is concentrated on a few powerful centralized node providers, the vision of Web3 – a decentralized and fairer internet – is compromised.
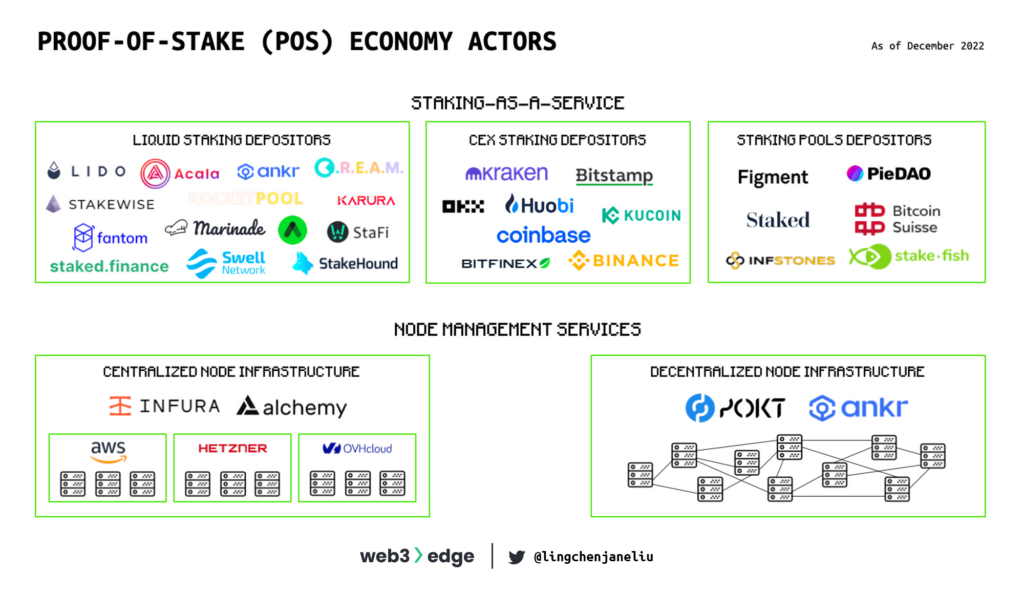
Staking-as-a-Service Providers
The high capital requirements (32 ETH), technical complexity around setting up a validator node, and extended staking lockup period (six months to one year after The Merge) stand in the way of ETH holders’ ability and willingness to stake. The birth of Staking-as-a-Service is to address those issues.
Staking-as-a-Service providers set up, maintain, and run the hardware and day-to-day operations of validators.
Validators play a key role in maintaining and securing blockchains. Validators, similar to miners in proof-of-work blockchains, are blockchain nodes in charge of processing, confirming and writing transactions into a new block. Every Proof-of-Stake based blockchain has validators who compete to perform those tasks in order to earn a share of the protocol’s revenue from transaction fees and from protocol’s security budget.
The staking rewards can be categorized into below two types:
- Transaction fees: A transaction fee is a standard charge included in crypto transactions to process the transaction on the blockchain.
- Protocol based rewards: Issuances from a global, protocol-defined, inflation rate.
Ethereum, Solana, Avalanche, Polkadot, Cardano network use a Proof-of-Stake consensus mechanism (PoS) and validators on the network have an opportunity to participate in consensus by casting votes for which blocks they believe should be added to the blockchain, thereby confirming any valid transactions contained in those particular blocks.
However, not all validators’ votes are weighted equally. The consensus votes of validators are stake-weighted, meaning the more stake an individual validator has, the more influence that one validator has in determining the outcome of the consensus voting. Similarly, validators with less stake have less weight in determining the vote outcome.
What is consensus voting?
Voting-based consensus mechanisms are democratic by nature, achieving consensus on transactions and key network decisions by counting the number of votes cast by nodes on the network.
Comparing Staking-as-a-Service Providers
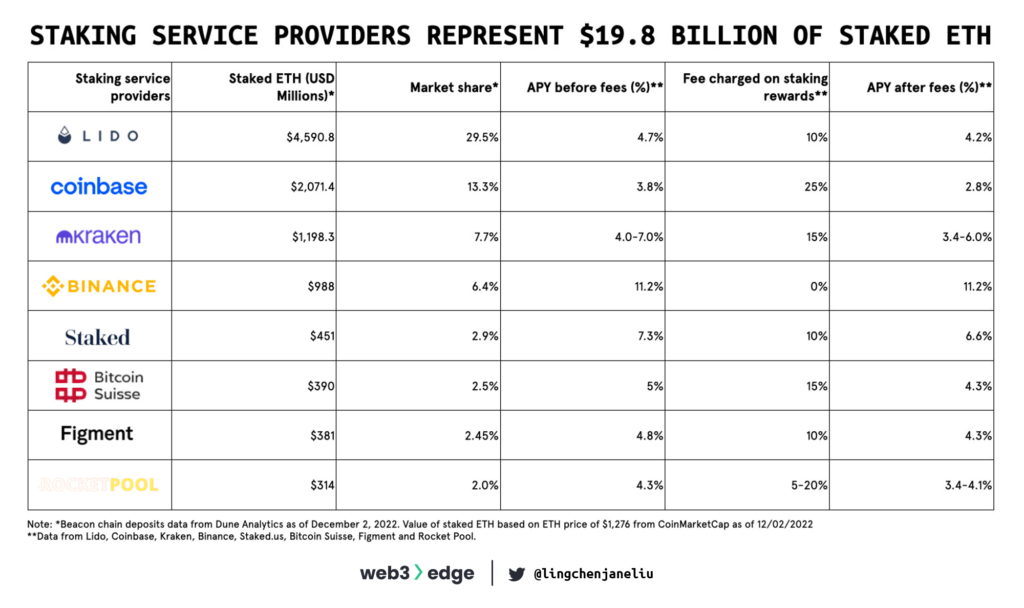
Staking-as-a-Service providers can be categorized into three types: liquid staking platforms, centralized exchange staking providers and staking pools. The table below provides an overview of the leading Ethereum staking service providers, including their current APY on staked ETH, the fees they charge, and their relative market share.
I will explain further the advantages, tradeoffs and the mechanisms of each type.
- Liquid staking providers
- Centralized exchange staking providers
- Staking pools
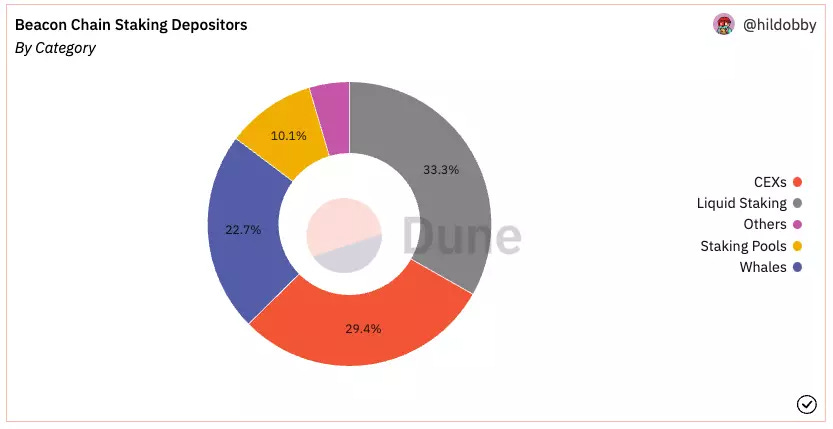
According to Dune Analytics, liquid staking has the highest market share, 33% (see below figure 8), among all categories. Staking service providers also represent more than 50% of total value staked on Ethereum.

Liquid staking providers
What is liquid staking?
Liquid staking enables people to stake to earn staking rewards and at the same time still have access to the liquidity of their tokens. Liquid staking protocols tokenize and issue on-chain representations of staked assets, which is called derivative staked tokens, that are a claim on underlying staking positions.
For example, when you stake ETH with Lido, you receive stETH in return and stETH represents your original position (see below figure 11).
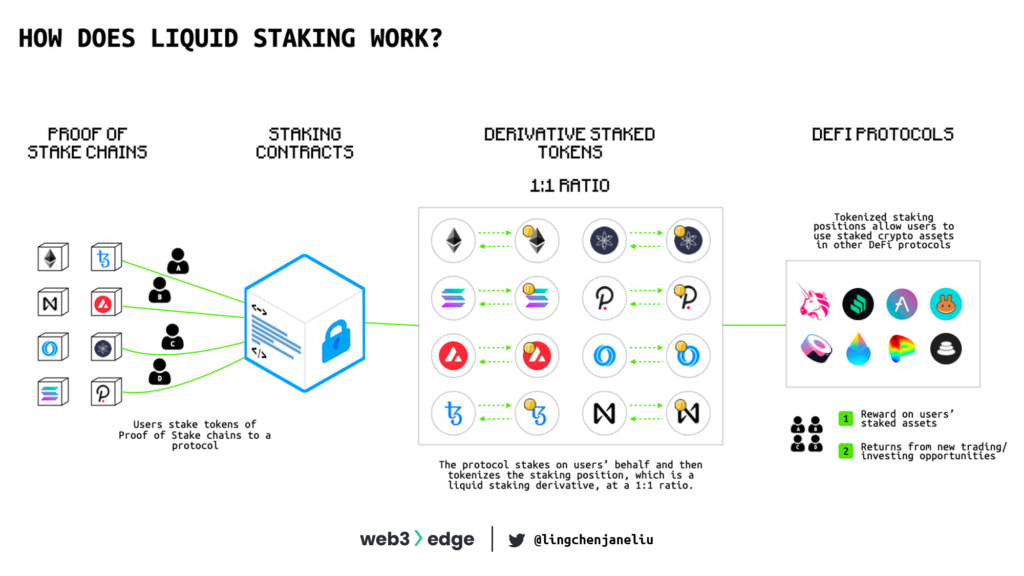
Why is liquid staking important?
Liquid staking protocols try to solve following problems that Proof-of-Stake networks have in common:
- Opportunity cost: With a derivative staked token, users can participate in DeFi and generate another layer of rewards on top of staking yields.
- Unbonding period: Since derivative staked tokens can be immediately swapped for their underlying staked assets, users don’t have to wait for the regular unbonding period to unstake their tokens.
- Reliance on a single validator: Liquid staking protocols usually delegate the staked tokens to various validators to diversify their exposure and minimize risk in the case that one single validator performs maliciously causing a slashing penalty.
What is a slashing penalty?
Slashing is a mechanism put in place to enforce good behavior. It is an irreversible punishment that slashes a percentage of an offending validator’s current stake. It results in a steady loss of ETH over time until the network forcibly evicts the validator and labels them “slashed”. Slashing prevents low-effort attacks like creating contradictory forks of validators attesting to past checkpoints.
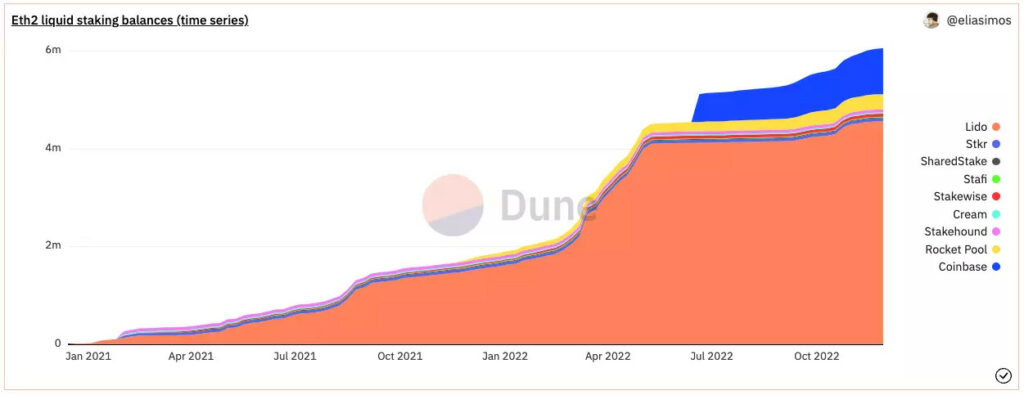
According to Dune Analytics, there are 33% of total staked ETH staked with liquid staking protocols with $8.3 billion in value. Among all the players, Lido and Rocket Pool are the biggest players with $5.8 billion and $273 million in value respectively locked. Other prominent players include Stakewise, Ankr, StakeHound, Cream, StaFi, etc. With Lido dominating the space, the concentration of staked ETH with this protocol generates concern that Lido could sabotage the security of the Ethereum network. According to Dune Analytics, in terms of staking value, Lido accounts for ~30% of total staked ETH. Due to the validator selection mechanism, Lido has been criticized that it is far more centralized than Rocket Pool Protocol.
Below I will scrutinize the validator selection mechanism between Lido and Rocket Pool. Liquid staking protocols like Lido and Rocket Pool are careful in selecting validators to work with, but their mechanisms vary.
Key Players
Lido: validator selection mechanism
Lido has a whitelist of industry-leading staking providers and keeps a community-owned scorecard to track the protocol’s staking performance. As Lido focuses on branding, reliability, visibility, and professionalism when it comes to node operator selections, it is prone for them to work with existing powerful node operators, which can lead to over-centralization. However, Lido has been working on easing the concern and launched a roadmap towards more decentralization.
Lido is currently a non-custodial and permissionless protocol for stakers so the greatest issue towards more decentralized lies in their node operator selection and management mechanism. Lido identifies three key parameters: lowest risk of downtime, censorship-resistance, and the highest expected throughput to evaluate a good validator set. Details of a robust and diverse validator set has following properties based on Lido’s definition of a good validator set. A good validator set allows users to use dApps on Ethereum Layer 1 and Layer 2s with the lowest risk of downtime or censorship, and the highest expected throughput. For that to happen, the validator set needs to deliver censorship resistance and performance.
- No operators with >1% of the total stake.
- An emphasis on improving client diversity in Ethereum.
- Legally and physically unrelated.
- Operators run their own nodes (no white-label or paid APIs in the infra).
- Operations are distributed geographically and jurisdictionally.
- Distributed variation of on-premise infra and different cloud providers.
- Good performance.
- Best practices in security and key management.
- Operators earn well enough to build a profitable, dependable business on staking.
- Long-term alignment with the success of Ethereum and decentralized economies.
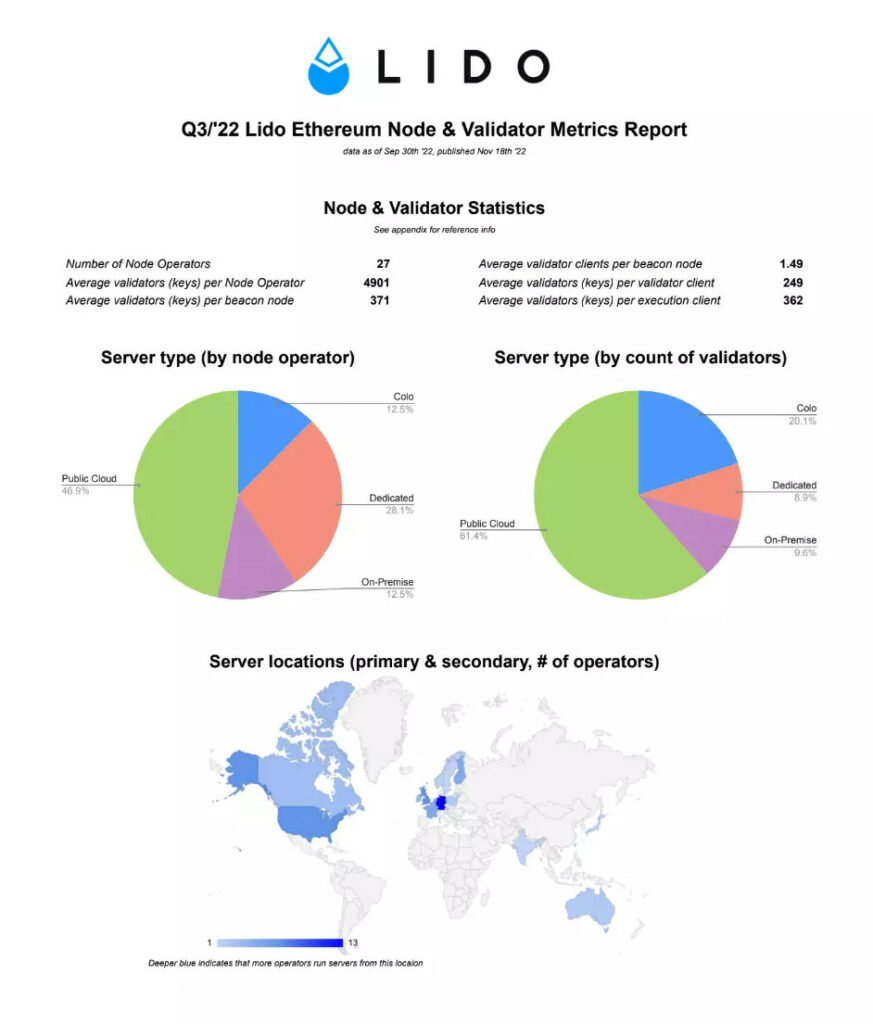
Lido has been working hard on examining its performance in terms of those properties and published quarterly reports to showcase its progress. Lido currently has 27 node operators. Those node operators run thousands of validators in various data centers around the world.
The detriment to decentralization is that the Lido DAO still has control of selecting node operators. To mitigate this concern, Lido has been adjusting its validator selecting process to a more permissionless manner. To get there, Lido proposed two fundamental improvements: the adoption of Distributed Validator Technology and the Creation of a Node Operator Score.
- Adoption of Distributed Validator Technology:
- What is it? The technology groups validators into independent committees that propose and attest to blocks together, greatly reducing the risk of an individual validator underperforming or misbehaving.
- Advantages: Distributed Validator Technology allow Lido to onboard untrusted node operators by pairing them with a majority of trusted node operators, resulting in a more decentralized and diverse group of nodes operating the network without compromising the security of Lido stakers and Ethereum.
- Creation of a Node Operator Score:
- What is it? Based on well-designed metrics to assign scores to node operators and allocate stake based on that. Currently, Lido distributes the same weights to different nodes operators and there is only binary nodes of trusted and untrusted node operators.Advantages: Implementation of Node Operator Score directly affects the protocol’s stake allocation and gives node operators incentive to maintain strong performance and integrity.
Lido’s business model
Revenue of Lido comes from the percentage of the staking rewards that Lido collects as a protocol fee. To collect the fee, the protocol mints new stETH token shares and assigns them to the fee recipients. Currently, the fee collected by Lido protocol is 10% of staking rewards with half of it going to the node operators and the other half going to the protocol treasury. For example, if you stake 10 ETH and you get 10 stETH in return, you receive 0.5 stETH over a year as staking rewards. You can keep 90% of the 0.5 stETH, the validator keeps 5% of the 0.5 stETH and Lido gets to keep the other 5% of the 0.5 stETH. In short, Lido’s revenue purely comes from its function of the staking rewards generated on its liquid staking derivatives.
With the biggest market share and its roadmap going towards greater decentralization, Lido is no doubt one of the strongest players in the staking economy. However, there is an emerging player – Rocket Pool – with a unique proposition and tokenomics.
Rocket Pool: validator selection mechanism
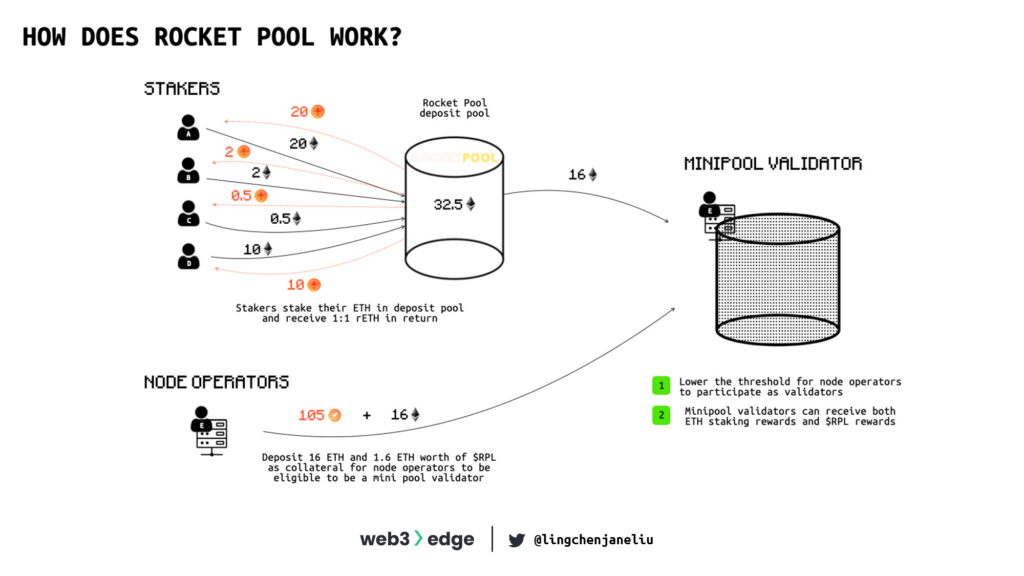
Rocket Pool aims to create a more decentralized staking solution set as it is quite capital and effort intensive to operate as a validator (needs high-scale hardware with 32 ETH deposited). To enable that, Rocket Pool designed an innovative mechanism by aggregating ETH from both node operators and Rocket Pool stakers. Node operators now only need to deposit 16 ETH per validator. This is coupled with 16 ETH from the staking pool, which stakers deposited in exchange for rETH, to create a new validator. This new validator is called a minipool.
User groups in Rocket Pool
- Smart Node Operators:
- You can operate as a smart node operator by holding only 16 ETH. After you provide 16 ETH and stake at least 10% of the validator’s ETH value in RPL (governance token of Rocket Pool) as a security promise to Rocket Pool, Rocket Pool will aggregate 16 ETH in user-deposited ETH for you to become a minipool validator. This unique mechanism enables node operators to become validators with less capital and facilitates the decentralization of the Ethereum network.
- Smart node operator can receive three types of compensation: RPL rewards, commission and staking rewards.
- RPL rewards: Node operators are eligible for RPL rewards, funded by RPL’s 5% emissions rate. RPL rewards are weighted by the proportion of total effective RPL posted as collateral.
- Commission: Node operators receive a 15% commission from stakers whose ETH is added to their minipool.
- Staking Rewards: Node operators can collect commission-free staking rewards for any ETH they have staked themselves.
- Stakers:
- Stakers can deposit as little as 0.01 ETH to the Rocket Pool deposit pool in return for rETH, the Rocket Pool liquid staking derivative token. rETH represents a user’s stake of ETH in the Rocket Pool Protocol, and rETH holders can collect staking rewards as Rocket Pool node operators generate those rewards. Once a staker deposits into the Rocket Pool protocol, deposits accumulate in the deposit pool, and 16 ETH of deposited ETH are matched with a node operator’s 16 ETH for a node operator to become a minipool validator.
- If you are more interested in Tokenomics, it is worth to look at Rocket Pool, which has 3.2% share of the liquid staking market and is the second largest among decentralized liquid staking players. Rocket Pool’s governance token, RPL, ties to the growth of the minipool as validators need to purchase 1.6 ETH worth of RPL to become minipool validators.
Swell Network: validator selection mechanism
Swell Network is a permissionless, non-custodial, and liquid ETH staking protocol. Swell aims to contribute to the Ethereum ecosystem making it more decentralised by lowering prerequisite capital for node operators and technical/infrastructure requirements for stakers to allow more to users participate in validating Ethereum 2.0 Proof-of-Stake blockchain.
There are a number of innovations that Swell devised to make Ethereum network more decentralized.
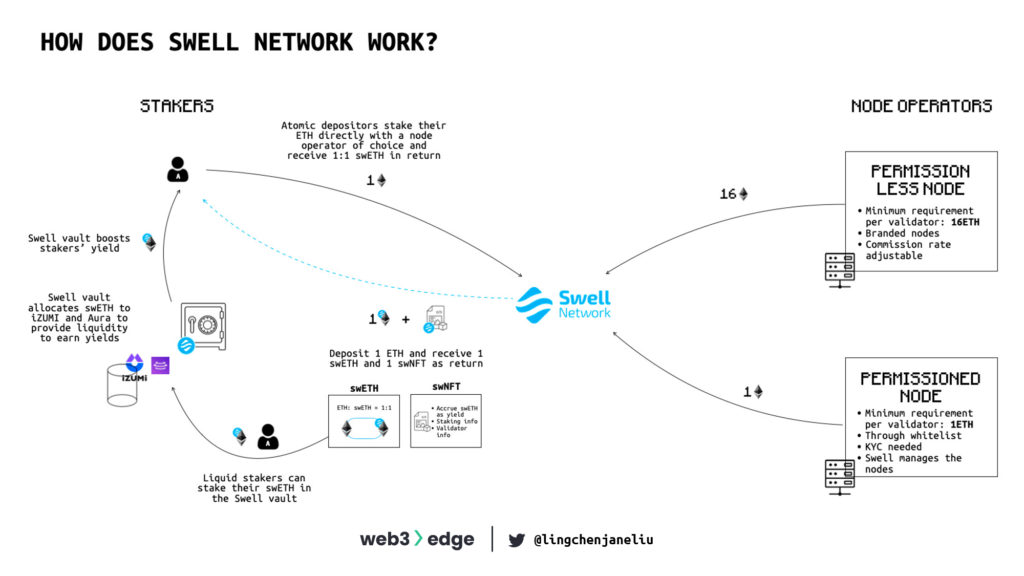
- Atomic deposits: Atomic deposits allow users to stake directly with a node operator of choice. The minimum stake is 1 ETH. Once users stake their ETH with Swell, swNFT and swETH are minted and returned to depositors. swNFT is a container that can hold the swETH and information about the stake, yield, and validator. swETH is returned 1:1 in terms of ETH deposited (principal).
- swETH: Liquid stakers on Swell receive a 1:1 staked ETH token called swETH. This token can be used in the DeFi ecosystem to earn extra yield.
- swNFT: Liquid stakers receive a minted financial NFT called swNFT, which contains all the metadata required to calculate staking rewards when you withdraw. Unlike some liquid staking protocols, the derivative swETH is not an interest-bearing token; it is only a receipt for your ETH staked into the Ethereum 2.0 staking contract.
- Swell vaults: swETH deposited in Swell vaults can earn extra yield for the depositors, which is quite similar to Yearn vaults.
- SSV Network: Swell has integrated a new Ethereum staking update, the Shared Secret Validator (SSV) — also known as Distributed Validator Technology (DVT). This upgrade reduces the financial commitment for running a node to as little as 1 ETH per validator, which is significantly lower than standard collateral of 32ETH and Rocket Pool’s required collateral of 16ETH.
Centralized exchange staking providers
Centralized exchanges, such as Binance, Kraken, OKX, Coinbase, Huobi also provide staking services. Even though some centralized exchange staking services offer higher APRs, there are downsides for staking on centralized entities.
When users stake with centralized entities, they do not receive a corresponding token in return (liquid staking derivatives) and, thus, lose the opportunity to perform any subsequent activity within DeFi. However, we see Binance launch bETH to tackle this downside.
Centralized exchanges usually have longer lock-up periods for stakers compared to decentralized liquid staking. The most concerning aspects of staking with centralized exchanges are asset security and overall health of blockchain network.
When users stake with centralized exchanges, their assets are in the custody of the centralized entities, and as recent FTX crisis should teach all of us a lesson: “Not your keys, not your coins“.
On top of that, you are giving up your voting right (your stakes) to those centralized entities and lose the chance to govern important issues related to the blockchain network.
Staking pools
Staking pools consolidate multiple Proof-of-Stake validators into one pool in order to increase the rewards earned through staking. Multiple users can lock their tokens to a single validator node, which allows the node’s smart contract to earn a larger share of the staking rewards due to the combined size of their staked capital.
The concept is similar to a mining pool which pools hashing power in a Proof-of-Work blockchain. Staking pools unite their staking power in the process of verifying and validating new blocks to gain a higher probability of earning block rewards. Prominent staking pools are Figment, Bitcoin Suisse, and Staked.us.
Staking pools can be either public or private, with each pool usually having a pool administrator who keeps the nodes or validators in operation. Digital assets are still staked in pools and often involve a lock-up period.
While some pools require users to stake their digital assets with a third party, there are many alternatives that allow users to contribute with their staking power while still holding their digital assets in a personal wallet. For instance, the so-called cold staking pools enable a more secure model, as users can participate in the staking process while keeping their funds on a hardware wallet.
Advantages of staking pools
- Flexibility and low entry barrier: If you don’t have a huge fund, pool staking is a reliable alternative way to make passive income as long as you have done your own your research and can ensure that you join a profitable pool.
- Low maintenance: Users do not need to worry about the technical implementation and maintenance of setting up and running a validating node.
Trade-offs
- Not fully transparent: Most staking pools do not involve smart contracts to manage and track users’ funds, which are managed off-chain. Liquid staking providers operate with smart contracts, where funds can be deposited to a contract, which trustlessly manages and tracks users’ stake, and issues users tokens that represent the value. This is not the case with for staking pools, where all activity is concentrated under system administrators.
The industry is moving towards a permissionless model
Node management service providers and Staking-as-a-Service providers are key cornerstones of the Proof-of-Stake economy, as they significantly lower the threshold for users to participate in the staking ecosystem and enable a more decentralized future. Even though the space is rather mature, we still see new players entering this space aiming at providing services in a more permissionless manner, such as Swell Network, to alleviate centralization issues of blockchain networks.
As more users and crypto communities raise concerns towards the censorship risk and contrary values node operators demonstrate when they heavily rely on centralized cloud providers, we see protocols and their communities have constant debates and consistent efforts to push development towards a more decentralized and permissionless manner for retail investors/users to participate in the staking ecosystem.
Closing
This piece was written by @lingchenjaneliu and edited by 0xPhillan for Web3edge! If you have any feedback about this piece or want to discuss its contents, reach out to @lingchenjaneliu on Twitter.
Subscribe to the Web3edge newsletter and never miss new content!
DISCLOSURE: THE AUTHOR MAY HAVE INVESTED AND MAY HOLD POSITIONS IN TOKENS MENTIONED IN THIS REPORT. THESE STATEMENTS ARE INTENDED TO DISCLOSE ANY CONFLICT OF INTEREST AND SHOULD NOT BE MISCONSTRUED AS A RECOMMENDATION TO PURCHASE ANY TOKEN. THIS CONTENT IS FOR INFORMATIONAL PURPOSES ONLY AND YOU SHOULD NOT MAKE DECISIONS BASED SOLELY ON IT. THIS IS NOT INVESTMENT ADVICE.
References
https://messari.io/report/governor-note-lido-and-l2
https://cms.stakingrewards.com/wp-content/uploads/2021/10/2021-Staking-Ecosystem-Report-1.pdf
https://blog.ethereum.org/2021/10/15/amphora-merge-milestone/
https://hackmd.io/@n0ble/the-merge-terminology
https://aws.amazon.com/blockchain/decentralization-in-blockchain/
https://ethereum.org/en/developers/docs/nodes-and-clients/
https://www.quicknode.com/guides/infrastructure/ethereum-full-node-vs-archive-node
SHARE THIS PIECE
Related content
The year of 2022 was a year of great highs and new lows for the Web3 industry. Read more about the defining events of 2022!
Metaverse Concept and History The term "metaverse" was invented by American author Neal Stephenson in his science fiction novel titled Snow Crash, published in 1992. ...
Short answer: Account abstraction creates a new account type which exists as a smart contract. By having the account exist as a smart contract, transaction ...
Wintermute, a crypto asset manager and liquidity provider, was recently hacked for US$160m. The hack occurred on their DeFi operations and did not affect other ...