23/09/22
The Wintermute Hack, What Happened?
Category
Written by
Read time
5 min
Hello world!
Hacks across Web3 have been making headlines this year:
- $625 million lost in hack of Axie Infinity’s sidechain Ronin (April, 2022)
- $325 million lost in hack of Wormhole, a cross-chain bridge (February, 2022)
- $182 million lost in hack of Beanstalk Farms, a DeFi project (April, 2022)
This week, a new hack took place that led to $160 million in losses for Wintermute, a crytpo asset manager and liquidity provider. In today’s newsletter we break down what happened.
This week 0xPhillan launched part one of his three-piece series Master Web3 Fundamentals. In his first part “From Node to Network“, 0xPhillan provides a comprehensive summary of the foundations of this fascinating industry.
____________
Understanding the Wintermute Hack
Wintermute, a crypto asset manager and liquidity provider, was recently hacked for US$160m. The hack occurred on their DeFi operations and did not affect other operations, according to Wintermute CEO Evgeny Gaevoy.
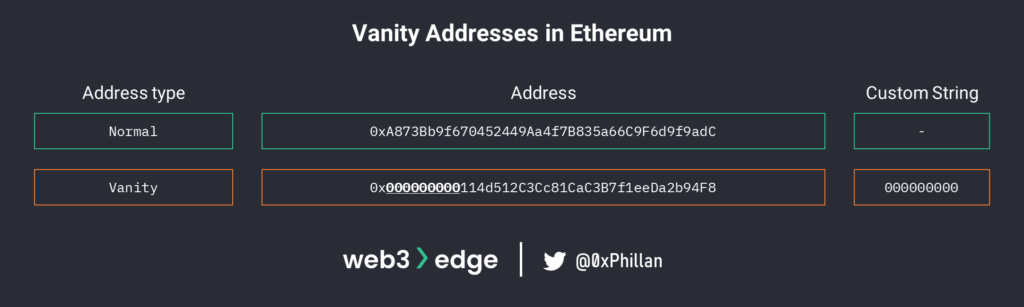
In this blog post, Mudit Gupta, Chief Security Officer at Polygon, points towards a vanity address generator called Profanity as being the source of the hack. A vanity address is an address which contains a user-defined character string. In Ethereum, the characters in addresses are limited to numbers and letters from A to F.
So, what happened?
Short answer
An Ethereum vanity address owned by Wintermute was compromised, which had admin privileges on a smart contract that controlled its DeFi funds.
Long answer
Let’s break down this hack using Mudit Gupta’s blog post, @YettyWapp’s Twitter thread and other news emerging as I write this.

On Jun 17th suspicious activity was detected on multiple deployer addresses. A deployer address is an externally owned address, also called EOA, which is an address created and used by a human, and not a smart contract. These unrelated deployer addresses claimed an airdrop for $FORTA and sent them to the same EOA address. That address dumped the airdrop for ETH tokens. This activity suggests one attacker was able to access multiple addresses, which points towards a common vulnerability.
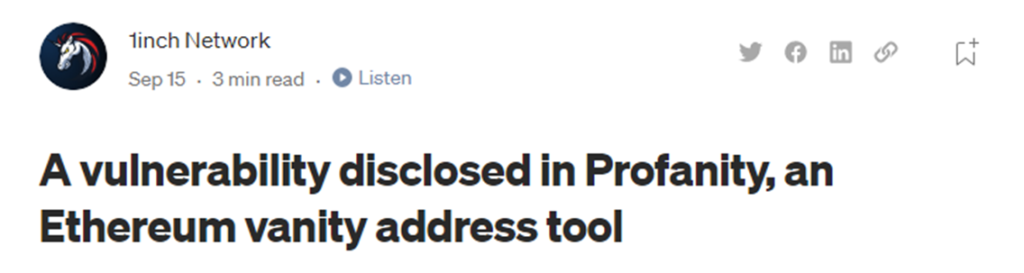
On Sep 17th the 1inch blog warned that addresses generated using the Profanity vanity address generator may be compromised, after it was found that addresses generated using the tool could be brute forced with the public key alone by reversing Profanity’s vanity address generation process.
When you generate a new Ethereum address and share it with other people, they cannot guess the public key from the address alone. However, as soon as you initiate a single transaction, the public key becomes visible on chain through the transaction signature.
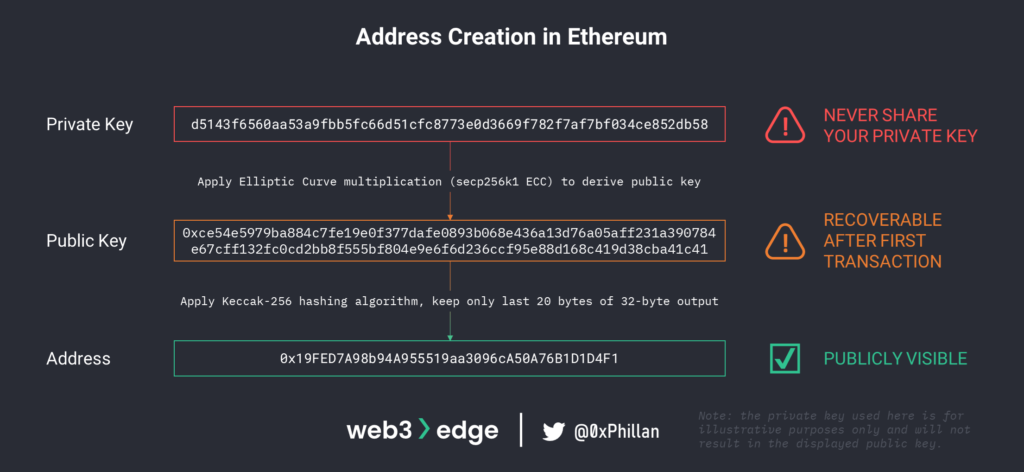
This means that as soon as the vanity address that was used to deploy the Wintermute vault smart contract, the public key became recoverable and the Profanity bug could be exploited.
Around the same time as the 1inch blog post, the remaining ether inside the vanity address was moved to another address; Evgeny points out that they were aware of this exploit and accelerated retiring less secure accounts.

Without any Ether in the address, the address cannot interact with the vault smart contract, since it needs to pay gas fees using Ether.
On Sep 20th, the attacker transferred 2 Ether into the vanity address. The vault smart contract has a setting to designate Ethereum addresses as administrators. Mudit explains that because the vanity address was never removed as an administrator, the address had full access to the vault smart contract.
With full access to the vault smart contract, the exploiter could interact with the vault and move out all funds to their personal wallet.
While Wintermute’s vanity address has been compromised, as of time of writing it has not yet been conclusively confirmed that this was a result of the Profanity bug. However, this appears to be most likely, with Wintermute CEO Evgeny Gaevoy suggesting the same and confirming their use of Profanity.
In his blog Mudit also writes:
“The attacker is likely a seasoned hacker/solidity developer. They created a helper contract, deposited stables into curve to avoid blacklisting, and figured out this vulnerability in a closed sourced vault contract in the first place.”
Despite the hack, Evgeny says that they are still solvent with over twice the amount of equity left. To come to an amicable agreement with the hacker, Evgeny proposes the hacker return a majority of the stolen funds and keep 16m USDC for themselves.
____________
Master Web3 Fundamentals: From Node to Network
Interested in Web3, blockchain and crypto, but don’t know where to begin? 0xPhillan has you covered! He wrote a comprehensive piece for newcomers and veterans covering the foundations of this fantastic industry: Master Web3 Fundamentals: From Node to Network.
This is the first part of a three-piece series that 0xPhillan is working on, covering the entire Web3 industry. If you’re not yet subscribed to our newsletter, sign up here to be notified when the next piece is ready!
____________
Knowledge Hub
Additional content to grow your edge and expand your horizon.
Technology
- Zero Knowledge Proof primer by Varun Shenoy
- Zero Knowledge Canon, part 1 & 2 by a16z
Design thinking
- Building Communities with a Unifying Vision by Derek Lau
- Market & Economic Structure of Games by @iandaog
Industry
- DuneCon recap and Dune API announcement by Dune
- VCs are shunning tokens, say veteran crypto investors by The Block
- Why equity plus token warrants is the new go-to formula for crypto VCs by The Block
____________
Today’s newsletter was written by @0xPhillan for Web3edge.io. Follow @Web3edge_io on Twitter!
____________
This newsletter is NOT financial advice, I am not a financial advisor. The information provided by Web3edge is for general informational and educational purposes only. Do your own research before investing. See Disclaimers for more information.
Was this newsletter forwarded to you? Sign up here.
SHARE THIS PIECE
Related content
Hello world! We are excited to announce the first guest piece published on Web3edge, by none other than the talented @lingchenjaneliu! In her piece she ...
Hello World! It's always good to reflect on where we came from, where we are and where we are going. With 2022 having come to ...
Web3edge Originals Hello World! The last few weeks the news cycle has been dominated with the collapse of the FTX exchange, FTX US exchange and Alameda ...
Hello World! This week we are taking a look at the metaverse, it's history and what the concept means when you strip away hype around ...




